Deeply understand the principles, types of SYN Flood attacks and their harm to servers, master a variety of defense measures, such as SYN cookies, traffic restrictions, load balancing, etc., to help enterprises...

When we are surfing the Internet, we may encounter inability to access the website, slow loading of the website, and lag in the game, which we usually think is a network speed problem.
In fact, this is just one possibility. Today, the Document will reveal another possibility to you - SynFlood flood attack.
SynFlood flood attack is also called SYN flooding, and is one of the classic attack methods of DDoS (Distributed Denial of Service).
SynFlood, like its name, uses flood-like Syn messages to attack the server, occupying the server's resources, causing the server to be unable to serve normal users.
When we encounter problems such as inaccessibility of the website, it may be because the server was hit by Syn flooding, which made it impossible to respond to our request.
Because an attacker can use tools to send a large number of Syn packets of variable source IP addresses or variable source ports to the server, even if the server's performance is enhanced or the server's connection capability is improved, it cannot withstand Syn flood attacks.
The key to defending SynFlood is to determine which connection requests come from abnormal users, so that the server can block requests from abnormal users, and ensure that normal users' business requests can be served.
SynFlood is a way to attack a server. It exhausts the server's resources by sending a large number of fake Syn messages to the server, thus preventing the server from responding to requests from normal users.
Then, the Syn message refers to the Synchronize message in the TCP protocol, which is the first message sent by the client to the server during the TCP three-time handshake.
To understand the attack methods of Syn Flood, first we will review the process of TCP three-time handshake:

First handshake: The client sends a Syn request message to the server, waiting for the server to confirm.
Second handshake: The server receives a Syn message and responds to a Syn-Ack request confirmation message.
Third handshake: The client receives the Syn-Ack message from the server and sends an Ack confirmation message to the server to indicate confirmation. After receiving the Ack message, the server completes three handshakes to establish a TCP connection.
In the above process, another important concept is that queues are not connected.
After the three-handshake, after receiving the Syn message from the client, the server will open an entry for the Syn message of each client in the unconnected queue.
This entry indicates that the server has received the Syn packet and sends a Syn-Ack message to the client. The server will delete the entry after the client replys to the Ack message or the connection timed out.
When the unconnected queue is full, the server cannot respond to other customers' requests.
SynFlood uses this mechanism of three handshakes in TCP connections. As shown in the figure below, the attack process of SynFlood is shown in the figure below:
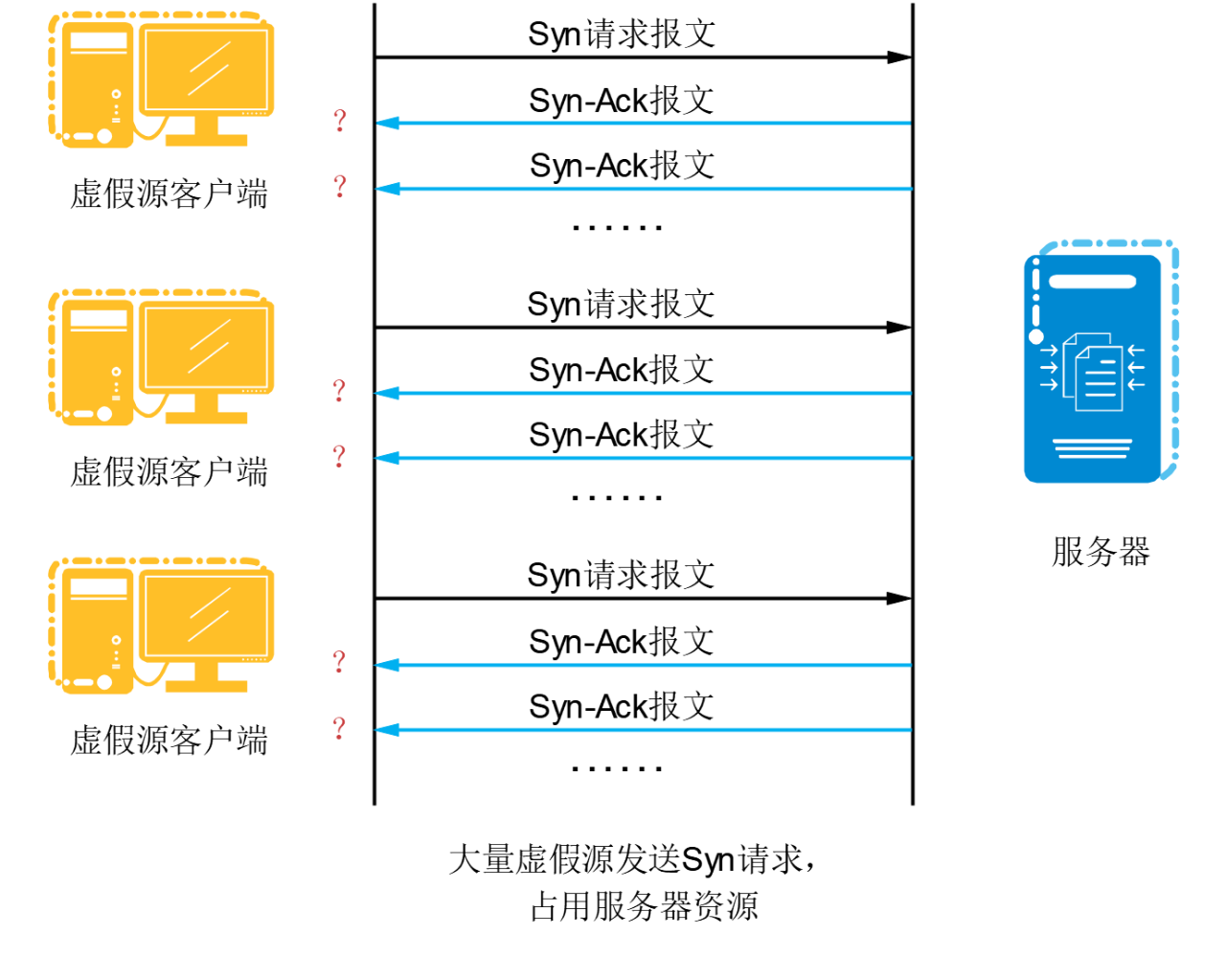
1.The attacker sends a large number of Syn messages to the server through the fake source IP address or port, requesting to establish a TCP connection.
2.The server receives a Syn message, responds to a Syn-Ack message and waits for user confirmation.
3.Because the source address does not exist, the server cannot receive the responding Ack message, and needs to send the Syn-Ack ack message repeatedly until the connection timeouts. These fake Syn packets will occupy the unconnected queue for a long time, making the server unable to respond to the Syn message requests of normal users.
It does not have much effect on synFlood's attacks that use massive Syn packets to capture server connection resources, improving the server's connection capabilities.
Therefore, these attack messages must be intercepted before they arrive at the server.
However, for security systems like firewalls, Syn messages are normal service messages, and the firewall cannot intercept them, otherwise the server will not be able to provide services to the outside world.
In addition, the firewall cannot clarify the IP address of the false source in advance, and use security policies to intercept Syn messages sent by these sources.
At this time, the capabilities of the Anti-DDoS system are required. The Anti-DDos system is deployed between the client and the server. It can process Syn messages before the server, identify false sources, block messages sent by these addresses, and only transmit legitimate Syn messages to the server.
The Anti-DDos system mainly processes Syn packets: source authentication and first packet discarding.
Source authentication
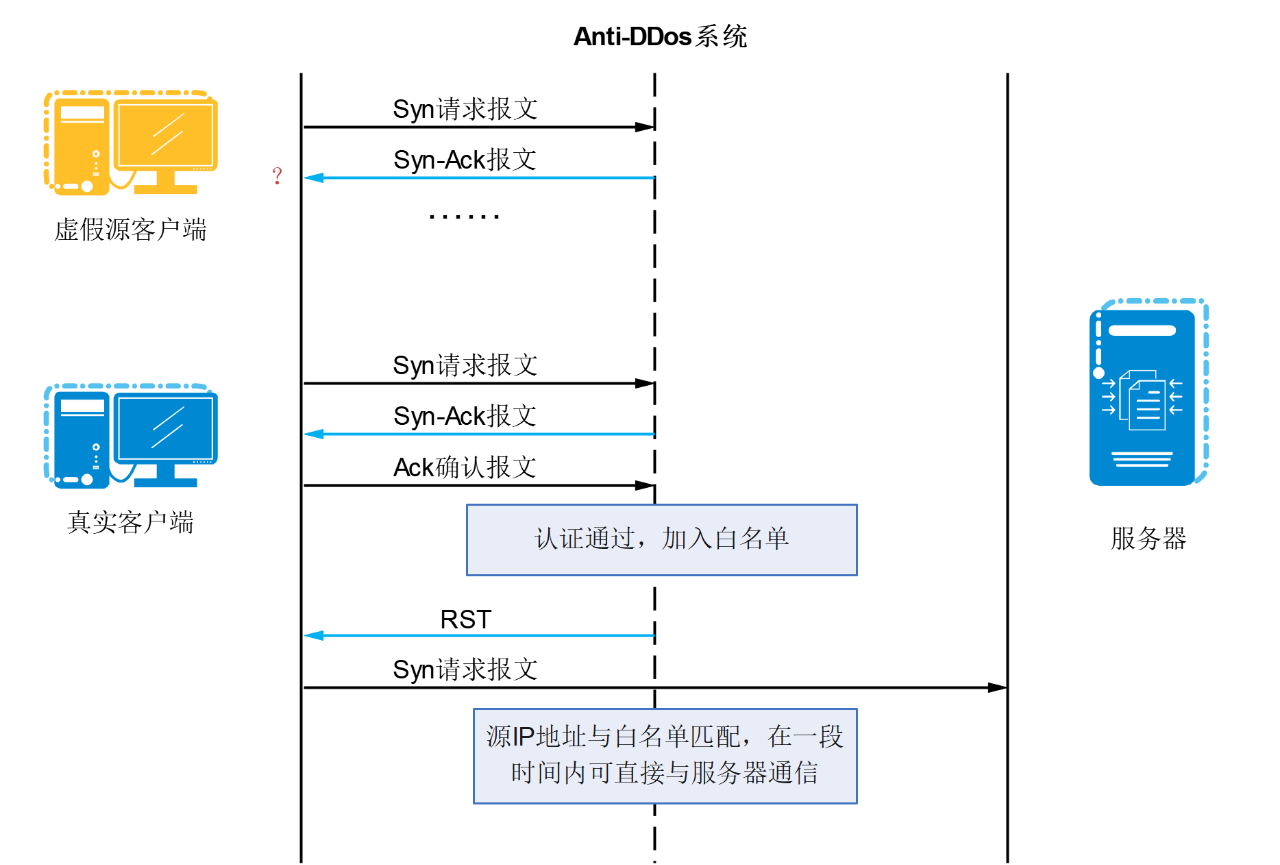
Anti-DDos system intercepts Syn messages sent by the client.
As shown in the figure below, under source authentication mode, the Anti-DDos system will send Syn-Ack messages to the client instead of the server. If the client does not respond, the client is considered to be a false source.
If the client answers, it is considered that the client is the real source, and the client is added to the whitelist, allowing all Syn messages sent by the client to pass through for a period of time.
But this method is actually to transfer the pressure of the server to the Anti-DDos system. Once the resources of the Anti-DDos system are consumed, the attack will still return to the server.
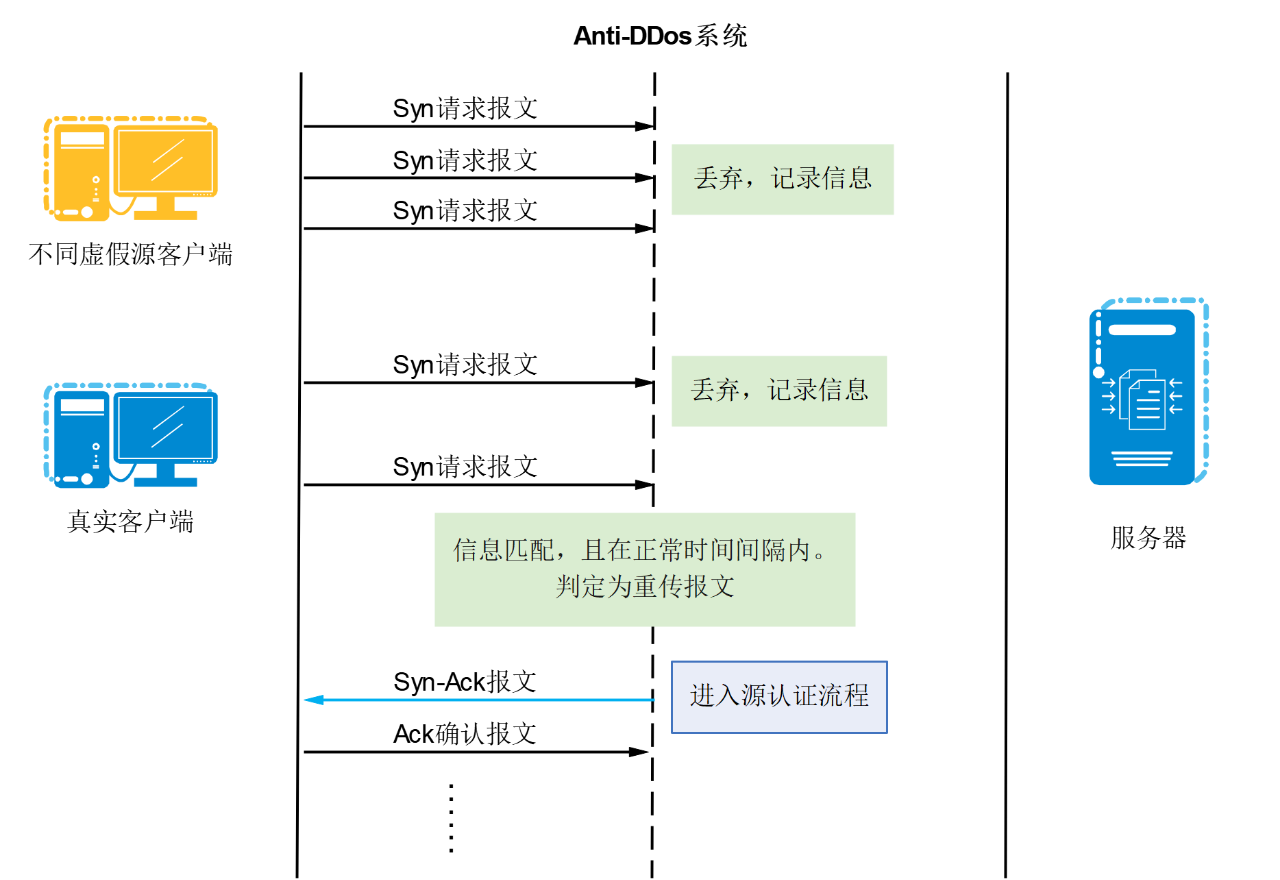
First packet discard
The reliability of the TCP protocol is not only reflected in the three-time mobile phone system, but also in the timeout and retransmission mechanism.
The way to discard the first packet is to use the TCP protocol reliability mechanisms of timeout and retransmission.
Just like if the server does not receive the client's Ack message for a long time, it will send the client again to the client, if the client does not receive the Syn-Ack message from the server for a long time after sending the Syn-Ack message, the client will also resend the Syn-Ack message to the server.
As shown in the figure below, the Anti-DDos system will discard the first Syn message sent by the client.
When the attacker launches a SynFlood attack, most of the Syn messages sent are variable-source Syn messages, so these Syn messages are the first packets for the Anti-DDos system and the system will be discarded directly. Only when the client retransmits the Syn message, Anti-DDos will perform source authentication on the message, which greatly reduces the pressure on the Anti-DDos system.
Using the combination of first packet discarding and source authentication, the server can effectively resist Syn Flood attacks, allowing the server to provide services to normal users.
-END-
The Internet world is like the home we enter and exit every day, and the Syn Flood attack is like a group of strangers ringing your doorbell crazy until you get upset.
Anti-DDos system is your home security guard, keeping you from being intruded by strangers.
For Syn Flood attacks, all we have to do is to choose APPs and websites with "security" with professional teams behind them to help fight the damage. We just have to surf with confidence
Source: ZTE Documentation Official Account
Preliminary review: Sand Fish Yin Hang
Re-examination: Xia Yan
Preliminary review: Zhang Danyang