Cyber threats appear every day, and some of them are difficult to prevent.

What is DDoS protection?
DDoS protection refers to measures to protect servers, networks, and stored data from DDoS attacks (a type of cyber attack).
DDoS attacks are mainly targeted at enterprises and may cause huge losses. Therefore, it is important to take thorough measures to prevent DDoS attacks and minimize losses when an attack occurs.
DDoS attack is the abbreviation of "distributed denial of service attack". This is a malicious attack in which no specified number of devices sends a large number of access requests to the website server at the same time, causing excessive load on the server and causing downtime.
Usually, a website is designed to process a certain amount of data traffic. DDoS attacks will send a large number of access requests at the same time, making the website unable to process it, causing serious impact on the operation of the website. By continuously sending request packets until the website service provider cannot bear it and crashes.
DDoS attacks use not only your own computing device, but also other people's computing devices. The initial attacker first infects other devices with malware and controls them.
A device infected with malware is called a "zombie machine", and an attack group composed of zombie machines is called a "zombie network". An attacker can then issue instructions to the botnet and manipulate it to launch an attack from a large number of devices.
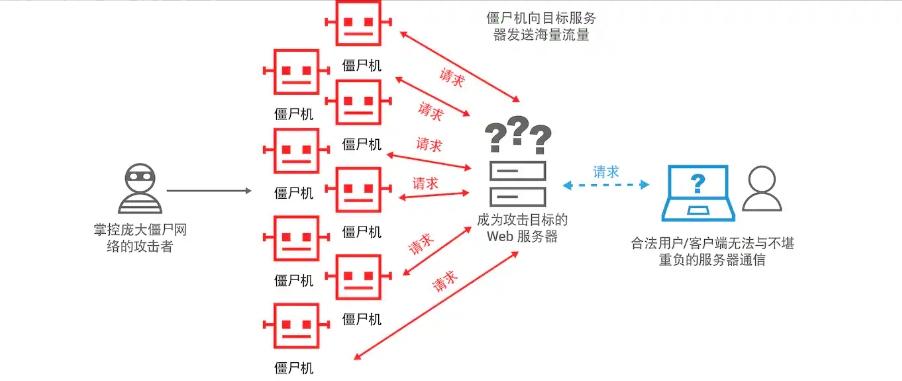
Image sourceakamai.com
An attack similar to DDoS attacks is DoS attacks. DoS attacks are abbreviation for "denial of service attacks" and refer to attacks that send large amounts of access or data to the target server.
DoS attacks are initiated from one computer, while DDoS attacks are initiated from multiple computers at the same time. Simply put, DDoS attack is an advanced form of DoS attack.
Reference reading: The difference between Dos and Ddos
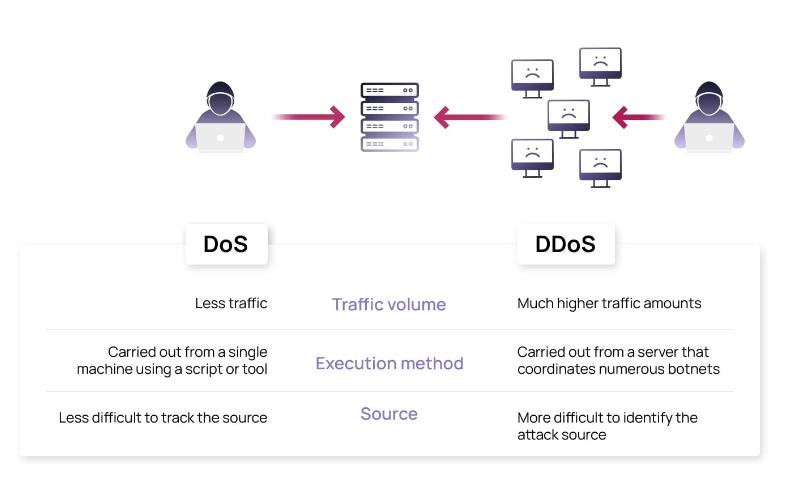
Compared with DoS attacks, DDoS attacks involve a large number of accesses from multiple sources, making the attack larger and the defense more complex.
DDoS attacks involve huge IP addresses, sometimes even reaching tens of millions. For DoS attacks, defense can be done by identifying and blocking attack IP addresses, but for DDoS attacks, it is difficult to identify the culprit because there are too many sources of attacks.
In the case of a DDoS attack, it is unrealistic to detect and block unauthorized access from all accesses.

Why are you suffering from DDoS attacks?
The purpose of launching a DDoS attack is to harass a specific company or destroy the business of a competitor company, so the company may become a target. In particular, companies that operate e-commerce websites or gaming sports companies and provide services through the Internet need to be careful.
The causes of DDoS attacks vary by situation and background, but generally speaking, attacks are often carried out due to the following factors:
Some DDoS The explicit purpose of the attack is not to undermine the credibility of a company or ask for money, but is just a form of mischief harassment that is intended to cause trouble to a particular company or organization.
In addition, DDoS attacks may also be initiated by individual dissatisfaction and protesting against the company's management philosophy or policies. DDoS attacks can also be used to demonstrate their ability to affect the operations of a company.
DDoS attacks are not uncommon not only carried out by individuals, but also by multi-person groups.
DDoS attacks may be a means adopted by competitors to disrupt their business. When a DDoS attack occurs, the website may be inaccessible or processing may be delayed, which may result in a loss of profits obtained from normal operations.
In addition, if the website is unavailable and the user's trust is lost, there is a risk that the customer will turn to another company. If a DDoS attack causes long-term disruption to your business, you may feel unsafe about your business and may even find yourself in trouble.
An opponents or those who are disgusted with something due to political belief differences or corporate scandals may launch a DDoS attack as a form of protest. Today, when computers are easily accessible to anyone, protests in cyberspace are not uncommon as a kind of demonstration.
Cyber attacks, especially attacks for political reasons, are called hacking activism. Hacktivism is a combination of the two words hacking and activism.
DDoS attacks are carried out as a form of ransomware. A typical example is when a DDoS attack causes a large-scale network outage, an attacker asks to pay in exchange for stopping the DDoS attack.
Recently, there have been many DDoS attacks in Japan, through which victims ransomware of virtual currencies. These attacks target small and medium-sized enterprises that do not take strong countermeasures and require businesses to pay money to block DDoS attacks.
Even if you pay for your business that is adversely affected, there is no guarantee that these malicious DDoS attacks will cease as promised. Also, you need to be careful as they may ask for more money.
When the server is damaged by a DDoS attack, the victim is forced to resume work. In addition, defense against cyber attacks may temporarily weaken during recovery. Attackers use this opportunity to launch cyber attacks, such as infecting systems with viruses or malware.
In addition to DDoS attacks, there are many types of cyber attacks, and it is not uncommon to combine multiple attacks. In some cases, an attacker may attempt to cover up the DDoS attack by first launching a DDoS attack and then launching another cyber attack when the victim takes corrective action against the DDoS attack.

DDoS attacks are attacks that crush a server or network by sending a large number of access requests. There are several different ways to use. There are five main types of DDoS attacks that are well known:
Every website in the world has its own IP address. An IP address is like an address on the Internet, allowing users to access the website.
However, since it is more troublesome for users to enter an IP address every time, they can access the website by name instead of the IP address, which is called "domain".
DNS is a function of converting domain names to IP addresses. DNS flood attacks overload DNS servers by sending a large number of return requests. If your DNS server does not work, your users will not be able to browse your website.
SYN Flood Attack and FIN Flood Attack are attack methods that utilize communication methods between two computers: SYN (connection request) and FIN (disconnection request). It sends a lot of data needed to connect and disconnect, consuming the resources required for server processing.
When an attack occurs, the system is too heavy to be loaded and it is difficult to access normally. This also makes unauthorized access more likely to occur.
In particular, if the company operating the network service becomes the target of the SYN flood attack, its services may be interrupted and the company's credibility may be lost. The computer you manage may also be used as a stepping stone and become an accomplice of the attack.
ACK Flood Attack is an attack that puts pressure on the target by sending a large number of ACKs (Acknowledgement Response). Typically, the connection source sends a connection request (SYN) or a disconnect request (FIN) to the destination, and when a response is received, an ACK (Acknowledgement) is sent to the destination.
However, because the ACK flood attack first passes the ACK (Acknowledgement response), the destination that was originally not connected will be in a state of rejection of the connection, thus putting pressure on the network.
UDP Flood Attack is initiated using a spoofed IP address. UDP is a mechanism for receiving data. When the server receives the UDP datagram, it will look for whether the program with the corresponding port number exists, and if it does not exist, it will notify the destination.
There are two types of UDP flood attacks: random port attacks and fragmented attacks.
Random port attacks include sending UDP datagrams with random port numbers, requiring victims to respond and continuously put pressure on them.
Fragment attack is an attack that sends a large amount of data to the target, increases the amount of unidentified data and puts pressure on the target.
Slow HTTP DoS attack is a general term for multiple DoS and DDoS attack methods that share common characteristics.
Typical DoS and DDoS attacks overwhelm the server's bandwidth and processing power by sending large amounts of packets to the target.
Slow HTTP DoS attacks, on the other hand, use relatively few packets to manipulate TCP sessions for a long time. This takes up the TCP session of the web server, thus preventing normal website visitors from accessing the site.
This technology is one of the most difficult attacks to prevent, where an attacker specifies a very small TCP window size to deliberately delay responses from a web server and keep the sessions persist for a long time.
If the DDoS attack exceeds the server's processing power, the server will crash and the website will be inaccessible. Even if the system does not crash, it will not work properly.
The damage caused by the DDoS attack is server downtime. When the server fails, in addition to repairing it, it also needs to investigate the cause and degree of damage. These tasks consume manpower, financial resources and time resources.
For example, performing a repair or inspection will affect the time for normal business operations. If there is insufficient staff, we need to hire personnel from other departments or outside the company.
Of course, the reduction in internal resources will also have an impact on business partners. This can lead to delays in delivery and production and, in some cases, even losses.
If the service is blocked due to a DDoS attack, the website or online store will not be available. This may cause the business to fail to secure sales. In particular, service disruptions will cause economic losses to companies whose main source of revenue is online sales.
Overload DDoS attacks can also damage server hardware and software. If the server fails and you need to fix it, or the resources are exhausted, you may need to add more resources, which can lead to unexpected costs.
In addition, if a DDoS attack destroys the service, it will damage the company's relationship with the customer. Customers will consider the service unreliable and turn to other websites, resulting in immeasurable financial losses.
In order to minimize losses when suffering from a DDoS attack, it is important to quickly identify that you may be suffering from a DDoS attack. If you suffer from a DDoS attack, you may notice something.
First, if your website loads slowly or receives error messages frequently, this can be a sign of a DDoS attack. In addition, unnatural increase in visits, such as multiple visits or repeated changes to pages from the same IP address in a short period of time, is also suspicious.
In addition, this may also be considered dangerous if the number of visits from overseas suddenly increases without obvious reasons. To minimize the damage caused by DDoS attacks, it is important to be careful and quickly detect the early symptoms of such attacks.

How to defend against DDoS attacks?
Unused and unnecessary ports and services may be entry points for attacks, so disabling them can reduce the vulnerability of the system.
Specifically, this involves disabling unused network services, closing unnecessary ports, disabling unused protocols, etc.
It is also important to regularly review service usage and establish an operating system that runs only the minimum necessary services. This reduces the surface area under attack and reduces security risks.
IP access restrictions are mainly used to prevent DoS attacks, but they cannot fully prevent DDoS attacks initiated from multiple IP addresses. But by defending against attacks from specific IP addresses, damage caused by DDoS attacks can be prevented.
In addition, if the DDoS attack source can identify the IP addresses that frequently launch attacks, blocking access to these IP addresses is also an effective countermeasure. As a defense against DDoS attacks, it is a good idea to consider IP access restrictions.
Stamping with access to specific countries is also effective. For example, for Japanese websites, restricting access to Japan is also an effective way to defend against DDoS attacks.
In addition, illegally seized IPs are often distributed around the world, so blocking access from specific countries is effective in mitigating DDoS attacks.
However, implementing restrictions not only denies access from attackers, but also from overseas users and general customers. It is important to set up your website or service in a way that suits your purpose.
Using CDN is also an effective solution. CDN is the abbreviation for "Contents Delivery Network", a way to distribute content by placing many servers around the world.
CDN's main purpose is to quickly deliver content, but due to the characteristics of using multiple cache servers, it is also effective in preventing DDoS attacks.
DDoS attack is an attack that exerts too much load on the target server. Therefore, if there are multiple servers, the load will be dispersed and an attack will not be possible.
To completely deal with DDoS attacks, using countermeasures tools specifically targeting DDoS attacks is effective. Among the response tools for DDoS attacks, the main product is WAF. WAF is the abbreviation of Web Application Firewall.
Detect attacks against web application vulnerabilities and block communication. This is an effective measure because it performs detailed analysis of data sent to the website in real time. They used to be very expensive, but recently there have also been low-cost cloud-based WAFs.
WAF stands for "Web Application Firewall" and is a security measure to protect web applications from cyber attacks. In this article, we will explain how WAF works, basic functions, advantages and disadvantages, and more in a way that is easy for beginners to understand.
DDoS attacks a large number of bots infected with malware, but measures are also required to prevent your company and its devices from becoming robots. If a robot is used as a stepping stone for attacks, it may become a complicit in attacks on related companies and others.
Specific countermeasures include constantly updating your operating system and applications to keep them up to date, enhancing security of your DNS servers, and setting filtering for sending and receiving emails.
It is important to take multiple measures. It is not only the possibility of becoming a target of the attack, but also the possibility of becoming a transit station for the attack.
DDoS attack is a cyber attack designed to adversely affect the operation of a service through a large number of Internet-connected devices while overloading a specific server or website.
DoS attacks are initiated from a single device, while DDoS attacks are a more advanced method of attack that is initiated from multiple devices at the same time. The losses caused by DDoS attacks are increasing year by year, and the targets of these attacks are very widespread, involving government agencies, general enterprises, online games, etc.
As a countermeasure to deal with DDoS attacks, we recommend disabling unnecessary services, blocking access from the same IP address or a specific country, using CDNs, and introducing DDoS attack countermeasures tools. To minimize losses in the event of a DDoS attack, be sure to take action using the methods described here.